- Google Hacking In Title Index Of Whatsapp Databases Download
- Google Hacking In Title Index Of Whatsapp Databases 2017
- Google Hacking In Title Index Of Whatsapp Databases 2018
- Google Hacking In Title Index Of Whatsapp Databases 2020
- Google Hacking In Title Index Of Whatsapp Databases
Name Last modified Size Description; Parent Directory - IMG-20131026-WA0000.jpg: 2020-05-23 21:50: 52K: IMG-20131027-WA0000.jpg. So here is WhatsApp Xtract v2.3 Released on April 25th, 2018 Tested with Whatsapp (Android) 2.18.46 Tested with Whatsapp (iPhone) 2.5.1 CHANGELOG: v2.3 (updated by ztedd - Apr 25, 2018). Google Scholar provides a simple way to broadly search for scholarly literature. Search across a wide variety of disciplines and sources: articles, theses, books, abstracts and court opinions. Yes, Google hacking should actually be called search engine hacking because it works with all search engines. Of course, specific queries for other search engines might be different. Access the Google hacking database, which contains search queries specific to Google. Google Dorks list 2020 can uncover some incredible information such as email addresses and lists, login credentials, sensitive files, website vulnerabilities, and even financial information (e.g. Payment card data). Also Read: Master in Ethical Hacking and Advanced Web Hacking Bundle.
That's when someone from our team suggested a post about this kind of data exposure issue. We've mentioned this type of security problem in previous posts, as it's a common source for security researchers to find valuable private information about any website.
Today we are going to dig into Google hacking techniques, also known as Google Dorks.
What is a Google Dork?
A Google Dork, also known as Google Dorking or Google hacking, is a valuable resource for security researchers. For the average person, Google is just a search engine used to find text, images, videos, and news. However, in the infosec world, Google is a useful hacking tool.
How would anyone use Google to hack websites?
Well, you can't hack sites directly using Google, but as it has tremendous web-crawling capabilities, it can index almost anything within your website, including sensitive information. This means you could be exposing too much information about your web technologies, usernames, passwords, and general vulnerabilities without even knowing it.
In other words: Google 'Dorking' is the practice of using Google to find vulnerable web applications and servers by using native Google search engine capabilities.
Unless you block specific resources from your website using a robots.txt file, Google indexes all the information that is present on any website. Logically, after some time any person in the world can access that information if they know what to search for. You can also access the Google Hacking Database (GHDB) which is the full Google dork list containing all Google dorking commands.
Important note: while this information is publicly available on the Internet, and it is provided and encouraged to be used by Google on a legal basis, people with the wrong intentions could use this information to harm your online presence.
Be aware that Google also knows who you are when you perform this kind of query. For this reason and many others, it's advised to use it only with good intentions, whether for your own research or while looking for ways to defend your website against this kind of vulnerability.
While some webmasters expose sensitive information on their own, this doesn't mean it's legal to take advantage of or exploit that information. If you do so you'll be marked as a cybercriminal. It's pretty easy to track your browsing IP, even if you're using a VPN service. It's not as anonymous as you think.
Before reading any further, be aware that Google will start blocking your connection if you connect from a single static IP. It will ask for captcha challenges to prevent automated queries.
Popular Google Dork operators
Google's search engine has its own built-in query language. The following list of queries can be run to find a list of files, find information about your competition, track people, get information about SEO backlinks, build email lists, and of course, discover web vulnerabilities.
Let's look at the most popular Google Dorks and what they do.
cache: this dork will show you the cached version of any website, e.g.cache:securitytrails.comallintext: searches for specific text contained on any web page, e.g.allintext: hacking toolsallintitle: exactly the same as allintext, but will show pages that contain titles with X characters, e.g.allintitle:'Security Companies'allinurl: it can be used to fetch results whose URL contains all the specified characters, e.g:allinurl:clientareafiletype: used to search for any kind of file extensions, for example, if you want to search for pdf files you can use:email security filetype: pdfinurl: this is exactly the same asallinurl, but it is only useful for one single keyword, e.g.inurl:adminintitle: used to search for various keywords inside the title, for example,intitle:security toolswill search for titles beginning with 'security' but 'tools' can be somewhere else in the page.inanchor: this is useful when you need to search for an exact anchor text used on any links, e.g.inanchor:'cyber security'intext: useful to locate pages that contain certain characters or strings inside their text, e.g.intext:'safe internet'site: will show you the full list of all indexed URLs for the specified domain and subdomain, e.g.site:securitytrails.com*: wildcard used to search pages that contain 'anything' before your word, e.g.how to * a website, will return 'how to…' design/create/hack, etc… 'a website'.|: this is a logical operator, e.g.'security' 'tips'will show all the sites which contain 'security' or 'tips,' or both words.+: used to concatenate words, useful to detect pages that use more than one specific key, e.g.security + trails–: minus operator is used to avoiding showing results that contain certain words, e.g.security -trailswill show pages that use 'security' in their text, but not those that have the word 'trails.'
If you're looking for the complete set of Google operators, you can follow this SEJ post which covers almost every known dork available today.
Google Dork examples
Let's take a look at some practical examples of the best Google hacks. You'll be surprised how easy is to extract private information from any source just by using Google hacking techniques.
Log files
Log files are the perfect example of how sensitive information can be found within any website. Error logs, access logs and other types of application logs are often discovered inside the public HTTP space of websites. This can help attackers find the PHP version you're running, as well as the critical system path of your CMS or frameworks.
For this kind of dork we can combine two Google operators, allintext and filetype, for example:
allintext:username filetype:log
This will show a lot of results that include username inside all *.log files.
In the results we discovered one particular website showing an SQL error log from a database server that included critical information:
This Google hack example exposed the current database name, user login, password and email values to the Internet. We've replaced the original values with 'XXX'.
Vulnerable web servers
The following Google Dork can be used to detect vulnerable or hacked servers that allow appending '/proc/self/cwd/' directly to the URL of your website.
inurl:/proc/self/cwd
As you can see in the following screenshot, vulnerable server results will appear, along with their exposed directories that can be surfed from your own browser.
Open FTP servers
Google does not only index HTTP-based servers, it also indexes open FTP servers.
With the following dork, you'll be able to explore public FTP servers, which can often reveal interesting things.
intitle:'index of' inurl:ftp
In this example, we found an important government server with their FTP space open. Chances are that this was on purpose — but it could also be a security issue.
ENV files
.env files are the ones used by popular web development frameworks to declare general variables and configurations for local and online dev environments.
One of the recommended practices is to move these .env files to somewhere that isn't publicly accessible. However, as you will see, there are a lot of devs who don't care about this and insert their .env file in the main public website directory.
As this is a critical dork we will not show you how do it; instead, we will only show you the critical results:
You'll notice that unencrypted usernames, passwords and IPs are directly exposed in the search results. You don't even need to click the links to get the database login details.
SSH private keys

SSH private keys are used to decrypt information that is exchanged in the SSH protocol. As a general security rule, private keys must always remain on the system being used to access the remote SSH server, and shouldn't be shared with anyone.
With the following dork, you'll be able to find SSH private keys that were indexed by uncle Google.
intitle:index.of id_rsa -id_rsa.pub
Let's move on to another interesting SSH Dork.
If this isn't your lucky day, and you're using a Windows operating system with PUTTY SSH client, remember that this program always logs the usernames of your SSH connections.
In this case, we can use a simple dork to fetch SSH usernames from PUTTY logs:
filetype:log username putty
Here's the expected output:
Email lists
It's pretty easy to find email lists using Google Dorks. In the following example, we are going to fetch excel files which may contain a lot of email addresses.
filetype:xls inurl:'email.xls'
We filtered to check out only the .edu domain names and found a popular university with around 1800 emails from students and teachers.
site:.edu filetype:xls inurl:'email.xls'
Remember that the real power of Google Dorks comes from the unlimited combinations you can use. Spammers know this trick too, and use it on a daily basis to build and grow their spamming email lists.
Live cameras
Have you ever wondered if your private live camera could be watched not only by you but also by anyone on the Internet?
The following Google hacking techniques can help you fetch live camera web pages that are not restricted by IP.
Here's the dork to fetch various IP based cameras:
inurl:top.htm inurl:currenttime
To find WebcamXP-based transmissions:
intitle:'webcamXP 5'
And another one for general live cameras:
inurl:'lvappl.htm'
There are a lot of live camera dorks that can let you watch any part of the world, live. You can find education, government, and even military cameras without IP restrictions.
If you get creative you can even do some white hat penetration testing on these cameras; you'll be surprised at how you're able to take control of the full admin panel remotely, and even re-configure the cameras as you like.
MP3, Movie, and PDF files
Nowadays almost no one downloads music after Spotify and Apple Music appeared on the market. However, if you're one of those classic individuals who still download legal music, you can use this dork to find mp3 files:
intitle: index of mp3
The same applies to legal free media files or PDF documents you may need:
intitle: index of pdfintext: .mp4
Weather
Google hacking techniques can be used to fetch any kind of information, and that includes many different types of electronic devices connected to the Internet.
In this case, we ran a dork that lets you fetch Weather Wing device transmissions. If you're involved in meteorology stuff or merely curious, check this out:
intitle:'Weather Wing WS-2'
The output will show you several devices connected around the world, which share weather details such as wind direction, temperature, humidity and more.
Zoom videos
'Zoom-bombing' became a popular means of disrupting online meetings in 2020 during the initial lockdown. The company has since placed some restrictions to make it harder to find/disrupt Zoom meetings, but long as a URL is shared, a Zoom meeting can still be found:
inurl:zoom.us/j and intext:scheduled for
The only drawback to this is the speed at which Google indexes a website. By the time a site is indexed, the Zoom meeting might already be over.
SQL dumps
Misconfigured databases are one way of finding exposed data. Another way is to look for SQL dumps that are stored on servers and accessible via a domain/IP.
Sometimes, these dumps appear on sites through incorrect backup mechanisms used by site admins who store backups on web servers (assuming that they aren't indexed by Google). To find a zipped SQL file, we use:
'index of' 'database.sql.zip'
We've omitted screenshots to avoid exposing any possible data breaches.
WordPress Admin
The view on whether to obfuscate your WordPress login page has arguments on both sides. Some researchers say it's unnecessary and using tools like a web application firewall (WAF) can prevent attacks much better than obfuscation would.
Finding WP Admin login pages is not too difficult with a dork:
intitle:'Index of' wp-admin
Apache2
This can be considered a subset of 'vulnerable web servers' mentioned above, but we're discussing Apache2 specifically because:
- LAMP (Linux, Apache, MySQL, PHP) is a popular stack for hosted apps/websites
- These Apache servers could be misconfigured/forgotten or in some stage of being setup, making them great targets for botnets
Find Apache2 web pages with the following dork:
intitle:'Apache2 Ubuntu Default Page: It works'
phpMyAdmin
Another risky yet frequently discovered tool on LAMP servers is phpMyAdmin software. This tool is another method of compromising data, as phpMyAdmin is used for the administration of MySQL over the web. The dork to use is:
'Index of' inurl:phpmyadmin
JIRA/Kibana
Google dorks can also be used to find web applications hosting important enterprise data (via JIRA or Kibana).
inurl:Dashboard.jspa intext:'Atlassian Jira Project Management Software'inurl:app/kibana intext:Loading Kibana
An easier way to find JIRA instances is to use a tool like SurfaceBrowser™, which can identify subdomains as well as the applications on those subdomains (besides JIRA, there are many other applications).
cPanel password reset
Another dork that can be used as the first step in reconnaissance is to hosted cPanels and then exploit various weaknesses in password resets to take over the cPanel (along with all the websites hosted on it). The dork for this purpose is:
inurl:_cpanel/forgotpwd
Government documents
Sensitive government documents are the last thing that should be exposed on the internet, but with dorks they aren't too hard to find, as shown below:
allintitle: restricted filetype:doc site:gov
Preventing Google Dorks
There are a lot of ways to avoid falling into the hands of a Google Dork.
These measures are suggested to prevent your sensitive information from being indexed by search engines.
- Protect private areas with a user and password authentication and also by using IP-based restrictions.
- Encrypt your sensitive information (user, passwords, credit cards, emails, addresses, IP addresses, phone numbers, etc).
- Run regular vulnerability scans against your site, these usually already use popular Google Dorks queries and can be pretty effective in detecting the most common ones.
- Run regular dork queries against your own website to see if you can find any important information before the bad guys do. You can find a great list of popular dorks at the Exploit DB Dorks database.
- If you find sensitive content exposed, request its removal by using Google Search Console.
- Block sensitive content by using a robots.txt file located in your root-level website directory.
Using robots.txt configurations to prevent Google Dorking
One of the best ways to prevent Google dorks is by using a robots.txt file. Let's see some practical examples.
The following configuration will deny all crawling from any directory within your website, which is pretty useful for private access websites that don't rely on publicly-indexable Internet content.
You can also block specific directories to be excepted from web crawling. If you have an /admin area and you need to protect it, just place this code inside:
This will also protect all the subdirectories inside.
Restrict access to specific files:
Restrict access to dynamic URLs that contain ‘?' symbol
To restrict access to specific file extensions you can use:
In this case, all access to .php files will be denied.
Final thoughts
Google is one of the most important search engines in the world. As we all know, it has the ability to index everything unless we explicitly deny it.
Today we learned that Google can be also used as a hacking tool, but you can stay one step ahead of the bad guys and use it regularly to find vulnerabilities in your own websites. You can even integrate this and run automated scans by using custom third-party Google SERPs APIs.
If you're a security researcher it can be a practical tool for your cybersecurity duties when used responsibly.
While Google Dorking can be used to reveal sensitive information about your website that is located and indexable via HTTP protocol, you can also perform a full DNS audit by using the SecurityTrails toolkit.
If you're looking for a way to do it all from a single interface—analyze your DNS records, zones, server IP map, related domains, subdomains as well as SSL Certificates—take a look into your SurfaceBrowser tool, request a demo with us today, or sign up for a free API account.
Esteban is a seasoned security researcher and cybersecurity specialist with over 15 years of experience. Since joining SecurityTrails in 2017 he's been our go-to for technical server security and source intelligence info.
Get the best cybersec research, news, tools,
and interviews with industry leaders
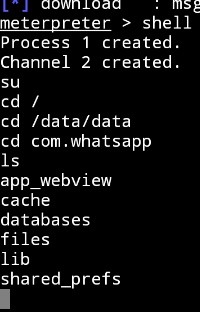
How to hack whatsapp data step by step. Intitle:'Index of' 'WhatsApp Databases'. And you can also perform this hack on your android device just open google.
At the moment, there are 1.3 billion Whatsapp users. This is a significant increase if you know that in 2016, the number was 1 billion. Obviously, due to simplicity and functionality, we can only assume that the number of users will go in one direction only, up!
But, this also means that a higher number of people will want to hack Whatsapp account. Yes, this is possible and there are 4 methods you can use.
Part 1. Hack whatsapp chat history:

Hack Someone's WhatsApp Messages without them Knowing Using Copy9
Copy9 is the first method on our list. Basically, it is a full-size app which allows you to get a complete access to a targeted device. In recent months, we have been able to see a huge increase in the number of users. They are parents and business owners, among others.
The main idea behind the app in question was to provide safety and security, rather than to use it for plain smartphone hacking, which is something we prefer. Yes, you can still hack Whatsappmessages and read them whenever you want.
Perhaps all of this spends complicated, but the real procedure is more than just simple. In essence, you will have to:
- Step 1: Download The Copy9 App
- Step 2: Install it on targeted device
- Step 3: Login to your control panel
As you can see, the entire process takes no more than 5 minutes of your time. It is specifically developed to be simple enough for average users and those who don't even fully understand smartphones and how they work. The bottom line is yes, you will be able to use it without a problem.
Here it should be mentioned that there is no risk of being detected! The app works by connecting to the operating system and literally becoming part of it. As such, the app has all the access to the OS on your phone, obviously.
The app cannot be detected by antivirus, malware software or on any other way. Hard reset of a device won't delete the app as well. At the end, we can add Copy9 is the safest app to use.
Besides the hack Whatsapp online feature, Copy9 offers plenty of additional features! Besides the fact you will be able to read Whatsapp messages, the app allows you to
- Read Messages and monitor calls performed via other apps.
- Tracking the GPS location is possible as well. The app will determine the exact location of a smartphone within a matter of seconds.
- Monitoring internet activities is just another feature. Although Whatsapp tracker option is associated with the internet, the feature here is a bit different.
- Basically, it allows for the user to block access to the web, limit it or check out what has been visited via the targeted device.
- In general, you will be able to monitor call, all messages, internet activity, detecting when a SIM card is changed and many other features.
Customer support is guaranteed and also more than just decent, which isn't a case with apps of this kind! The best part, you get a free trial, without a need to enter your credit card. If you don't like it, after 48 hours simply delete the app and you are done. However, most users who tried the free trial, have been using Copy9 ever since
Related:
Part 2: How to Hack a WhatsApp Account
You will probably want to obtain Whatsapp messages from a targeted device at some point. Although there are so many, different methods, not all of them are simple or effective. But, there is one which stands out from the crowd.
This method involves using the Whatsapp backup extractor. Hacking Whatsapp account is simple and fast, so anyone can use it. In addition, it works for iOS and for Android smartphones.
Hack whatsapp account on Iphone Using Whatsapp backup extractor for iOS devices
This is the most common application of the software in question. All you will have to do is to follow simple steps below. Keep in mind that you will need between 5 and 15 minutes to obtain the Whatsapp messages.
Step 1: Download and install dr.fone - Recover (iOS)
Step 2: Click on Repair button and select Whatsapp
Step 3: Click start scan and wait until it is done
In Title Index Of Movie
Step 4: Once again select files you want to recover
Once these files are on your computer, you will have a complete insight into the messages, media files and literally anything which was present in the backup file.
The software in question also works with iTunes and iCloud backups. With this method, you can hack Whatsapp messages without access to phone. Basically, the process is identical as we have mentioned earlier.
Step 1: Run dr.fone toolkit and click on repair
Step 2: Choose Recover from iTunes backup file and choose the latest backup
Step 3: Select Start scan
Step 4: Select files you want
Step 5: Recover them to your computer
After the procedure, all the files will be restored to your computer, including messages, media files and etc. In addition, this method is exactly the same as the first one here, but it uses backup file from iTunes rather than from the targeted device.
When it comes to iCloud extraction, the process is the same. But, you will have to log in to the iCloud account, select the suitable file and then follow the same steps as earlier.
Hack Someone's WhatsApp on Android without them Knowing by Using Whatsapp backup extractor
In this case scenario, you will have to use the dr.fone - Recover (Android) software. Luckily, the method is almost the same.
Step 3: Select Whatsapp messages and attachment files
Step 4: Click start scan (scan for all files is recommended)
Step 5: Recover files you want
There are two additional points we will have to mention here:
- The first one is the USB debugging option which must be activated before you start the process
- The second one is related to choosing between scan for all files or scan for deleted files
- It is up to you which type you will want, but we recommend scan for all files.
Part 3: Hack whatsapp by sending image
Related:
How actually safe Whatsapp and similar apps are? You may believe that they are bulletproof, but they aren't! As a matter of fact, both, Whatsapp and Telegram were able to be hacked by a single photo, yes, just one ordinary photo.
Both of these companies issue a new patch recently which should prevent this issue. According to the latest details, hackers were able to hack these accounts by sending a photo to a user.
Of course, a photo had to be opened, after which hack would be performed. The severity of this issue means that your account can be hacked within a matter of seconds. If you are looking for a wayhow to hack someone's Whatsapp without their phone this is the method for you.
Video Demonstration: The researchers also provided a video demonstration, given below which shows the attack in action.
In order to complete it, you will have to insert a malicious code into a photo. Once a user opens that photo, the code will infect the device, allowing you a complete access.
Within a matter of seconds, you can have a complete control over Whatsapp or Telegram, depending on which app you targeted. The explanation lies in the process how both of these apps treat media files.
The same applies to videos and documents, by the way. In essence, Whatsapp doesn't check the files for malware. It directly allows to the users to open, view and store a photo or a video.
In other words, the app will literally allow access of malware into a device. After which the account is hacked. A bit more detailed explanation is required here. Telegram, Whatsapp, and a few other apps use the same type of encryption.
It means that an app won't be aware of the message or a file which is sent to a device until it validates it. However, the opening is the first step here and only then a message is validated. In plain words, Whatsapp doesn't realize what has been actually received until it is too late.
Still, want to know how to hack a Whatsapp account using this method?
Google Hacking In Title Index Of Whatsapp Databases Download
Well, it may be still working among users who haven't upgraded their Whatsapp.
Google Hacking In Title Index Of Whatsapp Databases 2017
- Surprisingly, there are more than 60% of users who avoid or upgrade their apps as late as possible.
- Just in case, you will need a piece of code which can be implemented into a photo or a video.
- Once a victim opens the file, the code will spread through the device and infect it. Then, you will have a full control over the app.
- You can read the messages check out the contacts, delete anything you want and get access to private images and files!
This method does require knowledge of coding and it is one of the most complicated out there, simply due to the fact you will have to adapt the code according to several parameters. Dave and busters power card hack. On the other hand, the main advantage is in the further hacking capabilities.
In essence, once a hacked user sends the same photo to another, he will be hacked as well. This creates an impressive chain of hacked users, which can be more than just long.
Part 4: Hack whatsapp messages without access to phone
WhatsApp Tracker allows Hackers to Intercept and Read Your Encrypted Messages
This method is perhaps the most appealing of them all. In essence, it uses a 'backdoor' flaw. Some say it is a severe mistake, while others claim it is an additional feature.
Anyway, it allows to you to hack Whatsapp and to read, by intercepting the messages between users. Backdoor is used by Whatsapp, Telegram, and a few more apps. First of all, we should explain the end-to-end encryption. It means that you, as a user will send an encrypted message to another person.
Only after it is received, it will be decrypted and readable. Whatsapp introduced this feature in 2012 and then became the most secure app of them all. Sadly, it looks like it isn't so secure. Whatsapp is owned by Facebook, and if we know that this giant allows to the central intelligence agencies to spy on their users, we can deduce that Whatsapp shares the same flaw.
That's why the backdoor feature exists. Originally, it has been developed for central intelligence agencies, but at the same time, it is something that hackers can use. Furthermore, Whatsapp end-to-end encryption works on 'trust'. The company uses a secure server to process the messages, but according to the user agreement, they can change any of the rules at any given moment.
Basically, Whatsapp can choose to share your messages with others and you won't know about it!
The vulnerability relies on the way WhatsApp behaves when an end user's encryption key changes.
Basically, we have a scenario between users A and a person B. When a person A sends a few messages to the person B, the Whatsapp on that device will decrypt the messages and allow for the user to read them.
But, when a user B replaces the device, he will also be able to get and read those messages. This is possible due to the fact Whatsapp choose to update and modify the private keys, needed for decryption at any given moment, without informing the user.
Now, you as a hacker will be user C. You will modify the private key of a user B and insert your own. By doing so, you will directly be able to read messages of user A. Whatsapp spy app that can do it for you isn't so complicated to use, after all.
Here we have another advantage of this method. Facebook, which owns Whatsapp didn't solve this issue since 2016. It is obvious that it will stay available in the future as well.
All of this means that you, as a hacker will be able to exploit this method in the near future. Using Whatsapp tracker online and using this method will give impressive results. Some believe that backdoor feature is used as a feature to eliminate the need for constant privacy key verification, which is annoying. Instead, Whatsapp will do it instead of you.
But, Signal private messenger, which uses the same technology is immune to this issue, simply due to the fact it requires physical verification. If you are a decent hacker, you will be able to exploit this method or better said this drawback of the Whatsapp. After all, it is introduced to allow for agencies to spy on users, which means that hackers, including yourself, can use it for the same reason.
Conclusion
The best way to hack Whatsapp account is:
Obviously, it is Copy9 app.
First of all, it is so easy to use that you don't need any, precious knowledge or anything else. Even if you are an average user, you won't have any difficulties with it. Then we have the fact you will get additional features, which directly makes you the 'owner' of a targeted device.
Dalam surat Al-Anfal ayat 9 disebutkan: '(Ingatlah wahai Muhammad), ketika kamu memohon pertolongan kepada Tuhanmu lalu Dia mengabulkan permohonanmu.' (QS Al-Anfal:9). Pdf surat yasin dan tahlil nu. Di dalamnya termasuk kesehatan, keselamatan, harta, makanan, tempat tinggal, hewan tunggangan, dan segala hal yang dibutuhkan oleh seseorang. Sesuai di dalam Al-Qur'an atau hadits Nabi Muhammad SAW. Mayoritas orang yang melakukan istighosah dan do'a adalah dalam rangka meminta rizki. Dan rizki adalah sesuatu yang diberi atau dihadiahi.
On average, you will need around 5 minutes from the time you will download the app, install it and read the first Whatsapp messages.
The second method is a bit more demanding.

SSH private keys are used to decrypt information that is exchanged in the SSH protocol. As a general security rule, private keys must always remain on the system being used to access the remote SSH server, and shouldn't be shared with anyone.
With the following dork, you'll be able to find SSH private keys that were indexed by uncle Google.
intitle:index.of id_rsa -id_rsa.pub
Let's move on to another interesting SSH Dork.
If this isn't your lucky day, and you're using a Windows operating system with PUTTY SSH client, remember that this program always logs the usernames of your SSH connections.
In this case, we can use a simple dork to fetch SSH usernames from PUTTY logs:
filetype:log username putty
Here's the expected output:
Email lists
It's pretty easy to find email lists using Google Dorks. In the following example, we are going to fetch excel files which may contain a lot of email addresses.
filetype:xls inurl:'email.xls'
We filtered to check out only the .edu domain names and found a popular university with around 1800 emails from students and teachers.
site:.edu filetype:xls inurl:'email.xls'
Remember that the real power of Google Dorks comes from the unlimited combinations you can use. Spammers know this trick too, and use it on a daily basis to build and grow their spamming email lists.
Live cameras
Have you ever wondered if your private live camera could be watched not only by you but also by anyone on the Internet?
The following Google hacking techniques can help you fetch live camera web pages that are not restricted by IP.
Here's the dork to fetch various IP based cameras:
inurl:top.htm inurl:currenttime
To find WebcamXP-based transmissions:
intitle:'webcamXP 5'
And another one for general live cameras:
inurl:'lvappl.htm'
There are a lot of live camera dorks that can let you watch any part of the world, live. You can find education, government, and even military cameras without IP restrictions.
If you get creative you can even do some white hat penetration testing on these cameras; you'll be surprised at how you're able to take control of the full admin panel remotely, and even re-configure the cameras as you like.
MP3, Movie, and PDF files
Nowadays almost no one downloads music after Spotify and Apple Music appeared on the market. However, if you're one of those classic individuals who still download legal music, you can use this dork to find mp3 files:
intitle: index of mp3
The same applies to legal free media files or PDF documents you may need:
intitle: index of pdfintext: .mp4
Weather
Google hacking techniques can be used to fetch any kind of information, and that includes many different types of electronic devices connected to the Internet.
In this case, we ran a dork that lets you fetch Weather Wing device transmissions. If you're involved in meteorology stuff or merely curious, check this out:
intitle:'Weather Wing WS-2'
The output will show you several devices connected around the world, which share weather details such as wind direction, temperature, humidity and more.
Zoom videos
'Zoom-bombing' became a popular means of disrupting online meetings in 2020 during the initial lockdown. The company has since placed some restrictions to make it harder to find/disrupt Zoom meetings, but long as a URL is shared, a Zoom meeting can still be found:
inurl:zoom.us/j and intext:scheduled for
The only drawback to this is the speed at which Google indexes a website. By the time a site is indexed, the Zoom meeting might already be over.
SQL dumps
Misconfigured databases are one way of finding exposed data. Another way is to look for SQL dumps that are stored on servers and accessible via a domain/IP.
Sometimes, these dumps appear on sites through incorrect backup mechanisms used by site admins who store backups on web servers (assuming that they aren't indexed by Google). To find a zipped SQL file, we use:
'index of' 'database.sql.zip'
We've omitted screenshots to avoid exposing any possible data breaches.
WordPress Admin
The view on whether to obfuscate your WordPress login page has arguments on both sides. Some researchers say it's unnecessary and using tools like a web application firewall (WAF) can prevent attacks much better than obfuscation would.
Finding WP Admin login pages is not too difficult with a dork:
intitle:'Index of' wp-admin
Apache2
This can be considered a subset of 'vulnerable web servers' mentioned above, but we're discussing Apache2 specifically because:
- LAMP (Linux, Apache, MySQL, PHP) is a popular stack for hosted apps/websites
- These Apache servers could be misconfigured/forgotten or in some stage of being setup, making them great targets for botnets
Find Apache2 web pages with the following dork:
intitle:'Apache2 Ubuntu Default Page: It works'
phpMyAdmin
Another risky yet frequently discovered tool on LAMP servers is phpMyAdmin software. This tool is another method of compromising data, as phpMyAdmin is used for the administration of MySQL over the web. The dork to use is:
'Index of' inurl:phpmyadmin
JIRA/Kibana
Google dorks can also be used to find web applications hosting important enterprise data (via JIRA or Kibana).
inurl:Dashboard.jspa intext:'Atlassian Jira Project Management Software'inurl:app/kibana intext:Loading Kibana
An easier way to find JIRA instances is to use a tool like SurfaceBrowser™, which can identify subdomains as well as the applications on those subdomains (besides JIRA, there are many other applications).
cPanel password reset
Another dork that can be used as the first step in reconnaissance is to hosted cPanels and then exploit various weaknesses in password resets to take over the cPanel (along with all the websites hosted on it). The dork for this purpose is:
inurl:_cpanel/forgotpwd
Government documents
Sensitive government documents are the last thing that should be exposed on the internet, but with dorks they aren't too hard to find, as shown below:
allintitle: restricted filetype:doc site:gov
Preventing Google Dorks
There are a lot of ways to avoid falling into the hands of a Google Dork.
These measures are suggested to prevent your sensitive information from being indexed by search engines.
- Protect private areas with a user and password authentication and also by using IP-based restrictions.
- Encrypt your sensitive information (user, passwords, credit cards, emails, addresses, IP addresses, phone numbers, etc).
- Run regular vulnerability scans against your site, these usually already use popular Google Dorks queries and can be pretty effective in detecting the most common ones.
- Run regular dork queries against your own website to see if you can find any important information before the bad guys do. You can find a great list of popular dorks at the Exploit DB Dorks database.
- If you find sensitive content exposed, request its removal by using Google Search Console.
- Block sensitive content by using a robots.txt file located in your root-level website directory.
Using robots.txt configurations to prevent Google Dorking
One of the best ways to prevent Google dorks is by using a robots.txt file. Let's see some practical examples.
The following configuration will deny all crawling from any directory within your website, which is pretty useful for private access websites that don't rely on publicly-indexable Internet content.
You can also block specific directories to be excepted from web crawling. If you have an /admin area and you need to protect it, just place this code inside:
This will also protect all the subdirectories inside.
Restrict access to specific files:
Restrict access to dynamic URLs that contain ‘?' symbol
To restrict access to specific file extensions you can use:
In this case, all access to .php files will be denied.
Final thoughts
Google is one of the most important search engines in the world. As we all know, it has the ability to index everything unless we explicitly deny it.
Today we learned that Google can be also used as a hacking tool, but you can stay one step ahead of the bad guys and use it regularly to find vulnerabilities in your own websites. You can even integrate this and run automated scans by using custom third-party Google SERPs APIs.
If you're a security researcher it can be a practical tool for your cybersecurity duties when used responsibly.
While Google Dorking can be used to reveal sensitive information about your website that is located and indexable via HTTP protocol, you can also perform a full DNS audit by using the SecurityTrails toolkit.
If you're looking for a way to do it all from a single interface—analyze your DNS records, zones, server IP map, related domains, subdomains as well as SSL Certificates—take a look into your SurfaceBrowser tool, request a demo with us today, or sign up for a free API account.
Esteban is a seasoned security researcher and cybersecurity specialist with over 15 years of experience. Since joining SecurityTrails in 2017 he's been our go-to for technical server security and source intelligence info.
Get the best cybersec research, news, tools,
and interviews with industry leaders
How to hack whatsapp data step by step. Intitle:'Index of' 'WhatsApp Databases'. And you can also perform this hack on your android device just open google.
At the moment, there are 1.3 billion Whatsapp users. This is a significant increase if you know that in 2016, the number was 1 billion. Obviously, due to simplicity and functionality, we can only assume that the number of users will go in one direction only, up!
But, this also means that a higher number of people will want to hack Whatsapp account. Yes, this is possible and there are 4 methods you can use.
Part 1. Hack whatsapp chat history:
Hack Someone's WhatsApp Messages without them Knowing Using Copy9
Copy9 is the first method on our list. Basically, it is a full-size app which allows you to get a complete access to a targeted device. In recent months, we have been able to see a huge increase in the number of users. They are parents and business owners, among others.
The main idea behind the app in question was to provide safety and security, rather than to use it for plain smartphone hacking, which is something we prefer. Yes, you can still hack Whatsappmessages and read them whenever you want.
Perhaps all of this spends complicated, but the real procedure is more than just simple. In essence, you will have to:
- Step 1: Download The Copy9 App
- Step 2: Install it on targeted device
- Step 3: Login to your control panel
As you can see, the entire process takes no more than 5 minutes of your time. It is specifically developed to be simple enough for average users and those who don't even fully understand smartphones and how they work. The bottom line is yes, you will be able to use it without a problem.
Here it should be mentioned that there is no risk of being detected! The app works by connecting to the operating system and literally becoming part of it. As such, the app has all the access to the OS on your phone, obviously.
The app cannot be detected by antivirus, malware software or on any other way. Hard reset of a device won't delete the app as well. At the end, we can add Copy9 is the safest app to use.
Besides the hack Whatsapp online feature, Copy9 offers plenty of additional features! Besides the fact you will be able to read Whatsapp messages, the app allows you to
- Read Messages and monitor calls performed via other apps.
- Tracking the GPS location is possible as well. The app will determine the exact location of a smartphone within a matter of seconds.
- Monitoring internet activities is just another feature. Although Whatsapp tracker option is associated with the internet, the feature here is a bit different.
- Basically, it allows for the user to block access to the web, limit it or check out what has been visited via the targeted device.
- In general, you will be able to monitor call, all messages, internet activity, detecting when a SIM card is changed and many other features.
Customer support is guaranteed and also more than just decent, which isn't a case with apps of this kind! The best part, you get a free trial, without a need to enter your credit card. If you don't like it, after 48 hours simply delete the app and you are done. However, most users who tried the free trial, have been using Copy9 ever since
Related:
Part 2: How to Hack a WhatsApp Account
You will probably want to obtain Whatsapp messages from a targeted device at some point. Although there are so many, different methods, not all of them are simple or effective. But, there is one which stands out from the crowd.
This method involves using the Whatsapp backup extractor. Hacking Whatsapp account is simple and fast, so anyone can use it. In addition, it works for iOS and for Android smartphones.
Hack whatsapp account on Iphone Using Whatsapp backup extractor for iOS devices
This is the most common application of the software in question. All you will have to do is to follow simple steps below. Keep in mind that you will need between 5 and 15 minutes to obtain the Whatsapp messages.
Step 1: Download and install dr.fone - Recover (iOS)
Step 2: Click on Repair button and select Whatsapp
Step 3: Click start scan and wait until it is done
In Title Index Of Movie
Step 4: Once again select files you want to recover
Once these files are on your computer, you will have a complete insight into the messages, media files and literally anything which was present in the backup file.
The software in question also works with iTunes and iCloud backups. With this method, you can hack Whatsapp messages without access to phone. Basically, the process is identical as we have mentioned earlier.
Step 1: Run dr.fone toolkit and click on repair
Step 2: Choose Recover from iTunes backup file and choose the latest backup
Step 3: Select Start scan
Step 4: Select files you want
Step 5: Recover them to your computer
After the procedure, all the files will be restored to your computer, including messages, media files and etc. In addition, this method is exactly the same as the first one here, but it uses backup file from iTunes rather than from the targeted device.
When it comes to iCloud extraction, the process is the same. But, you will have to log in to the iCloud account, select the suitable file and then follow the same steps as earlier.
Hack Someone's WhatsApp on Android without them Knowing by Using Whatsapp backup extractor
In this case scenario, you will have to use the dr.fone - Recover (Android) software. Luckily, the method is almost the same.
Step 3: Select Whatsapp messages and attachment files
Step 4: Click start scan (scan for all files is recommended)
Step 5: Recover files you want
There are two additional points we will have to mention here:
- The first one is the USB debugging option which must be activated before you start the process
- The second one is related to choosing between scan for all files or scan for deleted files
- It is up to you which type you will want, but we recommend scan for all files.
Part 3: Hack whatsapp by sending image
Related:
How actually safe Whatsapp and similar apps are? You may believe that they are bulletproof, but they aren't! As a matter of fact, both, Whatsapp and Telegram were able to be hacked by a single photo, yes, just one ordinary photo.
Both of these companies issue a new patch recently which should prevent this issue. According to the latest details, hackers were able to hack these accounts by sending a photo to a user.
Of course, a photo had to be opened, after which hack would be performed. The severity of this issue means that your account can be hacked within a matter of seconds. If you are looking for a wayhow to hack someone's Whatsapp without their phone this is the method for you.
Video Demonstration: The researchers also provided a video demonstration, given below which shows the attack in action.
In order to complete it, you will have to insert a malicious code into a photo. Once a user opens that photo, the code will infect the device, allowing you a complete access.
Within a matter of seconds, you can have a complete control over Whatsapp or Telegram, depending on which app you targeted. The explanation lies in the process how both of these apps treat media files.
The same applies to videos and documents, by the way. In essence, Whatsapp doesn't check the files for malware. It directly allows to the users to open, view and store a photo or a video.
In other words, the app will literally allow access of malware into a device. After which the account is hacked. A bit more detailed explanation is required here. Telegram, Whatsapp, and a few other apps use the same type of encryption.
It means that an app won't be aware of the message or a file which is sent to a device until it validates it. However, the opening is the first step here and only then a message is validated. In plain words, Whatsapp doesn't realize what has been actually received until it is too late.
Still, want to know how to hack a Whatsapp account using this method?
Google Hacking In Title Index Of Whatsapp Databases Download
Well, it may be still working among users who haven't upgraded their Whatsapp.
Google Hacking In Title Index Of Whatsapp Databases 2017
- Surprisingly, there are more than 60% of users who avoid or upgrade their apps as late as possible.
- Just in case, you will need a piece of code which can be implemented into a photo or a video.
- Once a victim opens the file, the code will spread through the device and infect it. Then, you will have a full control over the app.
- You can read the messages check out the contacts, delete anything you want and get access to private images and files!
This method does require knowledge of coding and it is one of the most complicated out there, simply due to the fact you will have to adapt the code according to several parameters. Dave and busters power card hack. On the other hand, the main advantage is in the further hacking capabilities.
In essence, once a hacked user sends the same photo to another, he will be hacked as well. This creates an impressive chain of hacked users, which can be more than just long.
Part 4: Hack whatsapp messages without access to phone
WhatsApp Tracker allows Hackers to Intercept and Read Your Encrypted Messages
This method is perhaps the most appealing of them all. In essence, it uses a 'backdoor' flaw. Some say it is a severe mistake, while others claim it is an additional feature.
Anyway, it allows to you to hack Whatsapp and to read, by intercepting the messages between users. Backdoor is used by Whatsapp, Telegram, and a few more apps. First of all, we should explain the end-to-end encryption. It means that you, as a user will send an encrypted message to another person.
Only after it is received, it will be decrypted and readable. Whatsapp introduced this feature in 2012 and then became the most secure app of them all. Sadly, it looks like it isn't so secure. Whatsapp is owned by Facebook, and if we know that this giant allows to the central intelligence agencies to spy on their users, we can deduce that Whatsapp shares the same flaw.
That's why the backdoor feature exists. Originally, it has been developed for central intelligence agencies, but at the same time, it is something that hackers can use. Furthermore, Whatsapp end-to-end encryption works on 'trust'. The company uses a secure server to process the messages, but according to the user agreement, they can change any of the rules at any given moment.
Basically, Whatsapp can choose to share your messages with others and you won't know about it!
The vulnerability relies on the way WhatsApp behaves when an end user's encryption key changes.
Basically, we have a scenario between users A and a person B. When a person A sends a few messages to the person B, the Whatsapp on that device will decrypt the messages and allow for the user to read them.
But, when a user B replaces the device, he will also be able to get and read those messages. This is possible due to the fact Whatsapp choose to update and modify the private keys, needed for decryption at any given moment, without informing the user.
Now, you as a hacker will be user C. You will modify the private key of a user B and insert your own. By doing so, you will directly be able to read messages of user A. Whatsapp spy app that can do it for you isn't so complicated to use, after all.
Here we have another advantage of this method. Facebook, which owns Whatsapp didn't solve this issue since 2016. It is obvious that it will stay available in the future as well.
All of this means that you, as a hacker will be able to exploit this method in the near future. Using Whatsapp tracker online and using this method will give impressive results. Some believe that backdoor feature is used as a feature to eliminate the need for constant privacy key verification, which is annoying. Instead, Whatsapp will do it instead of you.
But, Signal private messenger, which uses the same technology is immune to this issue, simply due to the fact it requires physical verification. If you are a decent hacker, you will be able to exploit this method or better said this drawback of the Whatsapp. After all, it is introduced to allow for agencies to spy on users, which means that hackers, including yourself, can use it for the same reason.
Conclusion
The best way to hack Whatsapp account is:
Obviously, it is Copy9 app.
First of all, it is so easy to use that you don't need any, precious knowledge or anything else. Even if you are an average user, you won't have any difficulties with it. Then we have the fact you will get additional features, which directly makes you the 'owner' of a targeted device.
Dalam surat Al-Anfal ayat 9 disebutkan: '(Ingatlah wahai Muhammad), ketika kamu memohon pertolongan kepada Tuhanmu lalu Dia mengabulkan permohonanmu.' (QS Al-Anfal:9). Pdf surat yasin dan tahlil nu. Di dalamnya termasuk kesehatan, keselamatan, harta, makanan, tempat tinggal, hewan tunggangan, dan segala hal yang dibutuhkan oleh seseorang. Sesuai di dalam Al-Qur'an atau hadits Nabi Muhammad SAW. Mayoritas orang yang melakukan istighosah dan do'a adalah dalam rangka meminta rizki. Dan rizki adalah sesuatu yang diberi atau dihadiahi.
On average, you will need around 5 minutes from the time you will download the app, install it and read the first Whatsapp messages.
The second method is a bit more demanding.
You will need to know the essence of coding. But, this isn't something you can learn at school or at some other place. You will have to be born for this and you will need to understand the matter without the help of anyone else. Also, once users upgrade the app, you won't be able to use this method anymore.
The third, backdoor method is still possible and it will stay possible ever since, due to the fact Facebook refuses to change the privacy terms!
In other words, you will be able to use it as long as you want. But, this method is also complicated and probably even more demanding than the second one here. So, if you choose to use it, take your time, learn the matter and only then try it. By the way, this method can be detected easily by users!
At the end, we should repeat that the best and the easiest way is to use Copy9. It doesn't require any of the requirements other two methods do, but it offers even better result.
Google Hacking In Title Index Of Whatsapp Databases 2018
In Title Index.of Mp3 Downloads
Google Hacking In Title Index Of Whatsapp Databases 2020
Get a Free Trial copy9 Now: hack whatsapp with copy9
Google Hacking In Title Index Of Whatsapp Databases
Or Buy Copy9 Now and Start Monitoring Within Minutes: Buy Now

